-
Notifications
You must be signed in to change notification settings - Fork 11
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Stack corruption on keypair generation #40
Comments
|
AddressSanitizer report on the openarray branch: 49bed1a You may need to add Note that seckey should be lesser than the CurveOrder so there is at least one error earlier than the stacktrace The incriminated nim-blscurve/blscurve/csources/64/ecp_BLS381.c Lines 1056 to 1061 in 9a14335
|
|
For some reason Milagro cannot take the modulo of this import blscurve/[milagro, common]
proc main() =
var okm: BIG_384
doAssert okm.fromHex"7e65031cc69d8847cc1dab551b7b3b273167c64ccb50432062f3f06d59a8048f4d62360c7914c49a79b16f090b3f0a88"
debugEcho "CurveOrder: ", CURVE_Order.toHex()
var seckey = okm
BIG_384_mod(okm, CURVE_Order)
echo "seckey: ", seckey
main() |
The stack can be corrupted on key-pair generation.
For some reason this does not happen when generated in a loop, for example
But it happens when generated in global arrays (even on the heap) like in PR status-im/nimbus-eth2#780 unless it has to do with object variants?
In Clang
This seems to manifest as a secret key that is bigger than the curve order:
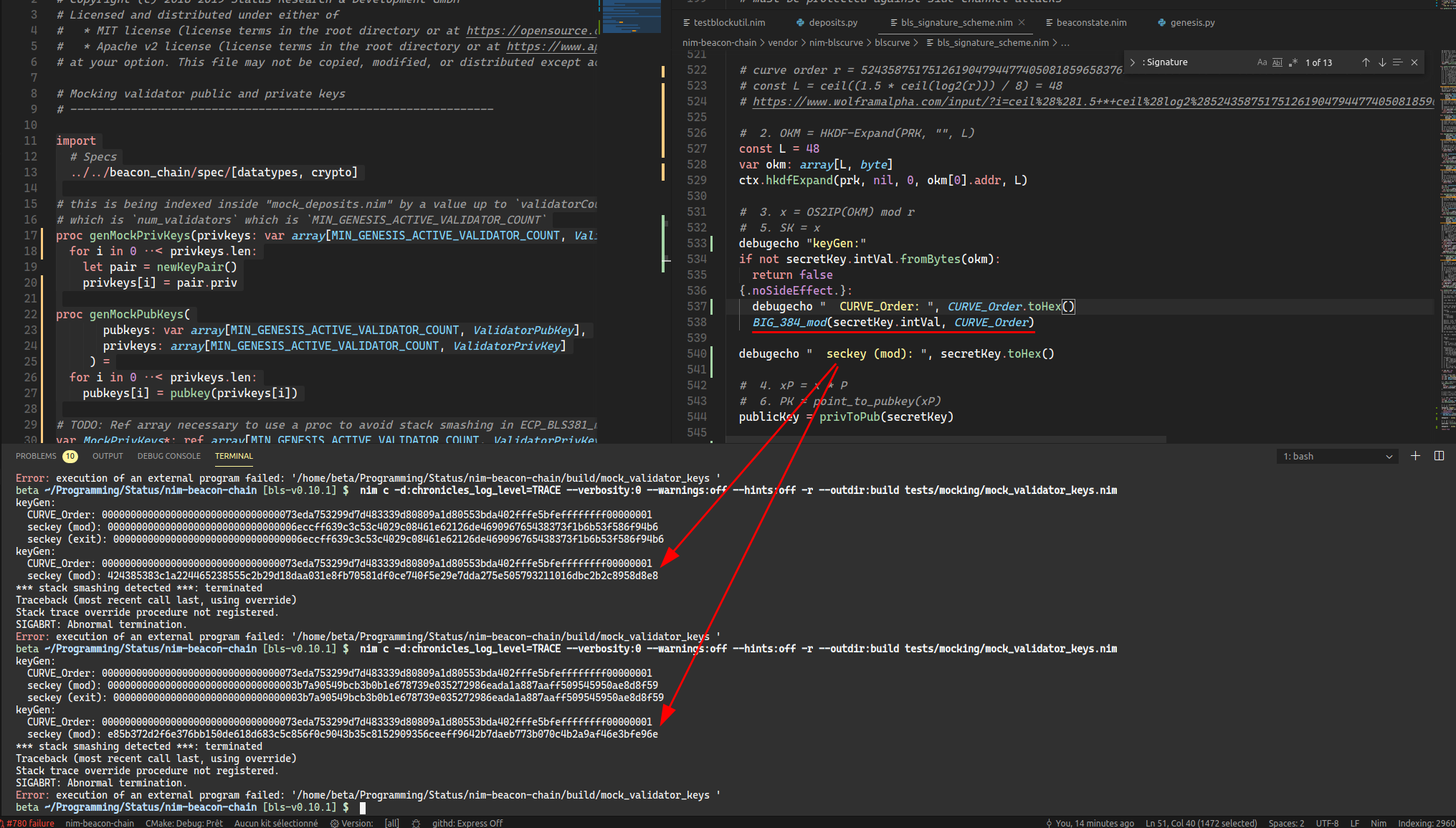
In GDB we crash soon after
The text was updated successfully, but these errors were encountered: