This extension is not developed, maintained or supported by SailPoint. It is a community effort to help manage Identity Security Cloud from Visual Studio Code.
The SailPoint Identity Security Cloud extension makes it easy to:
- Connect to several tenants
- Import and export config of a tenant
- View, edit, aggregate, test, peek, ping, clone, or reset sources
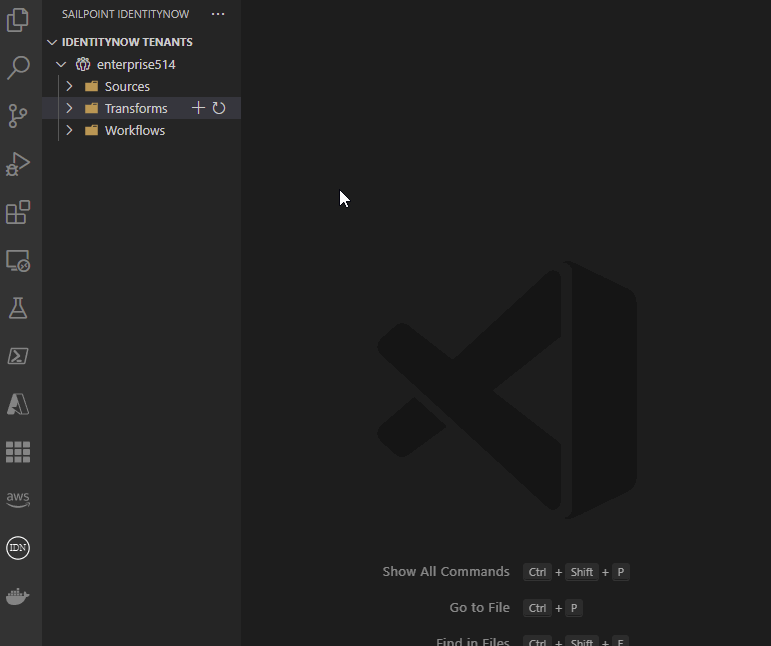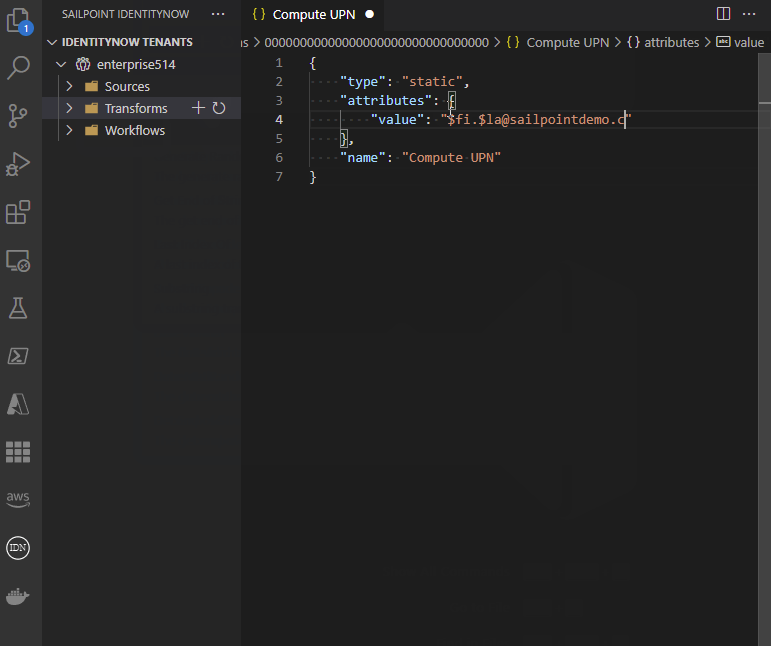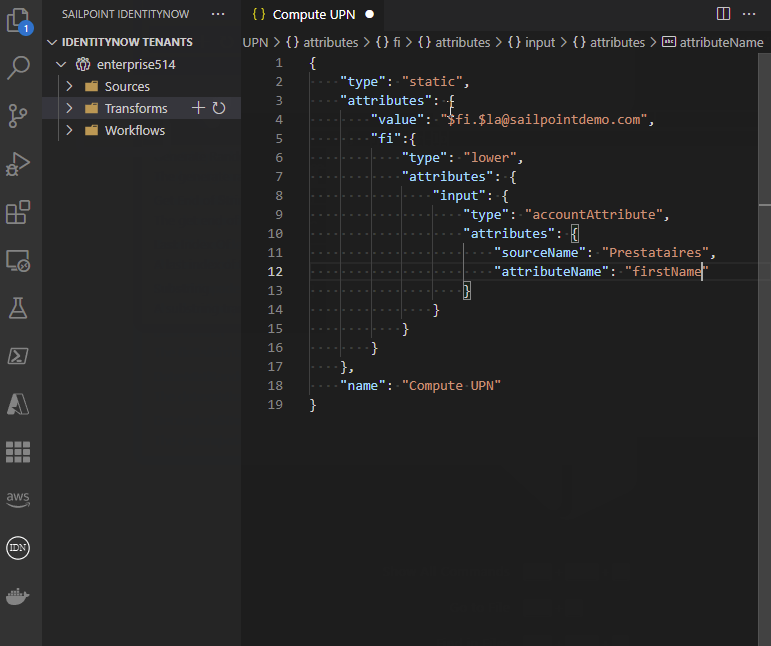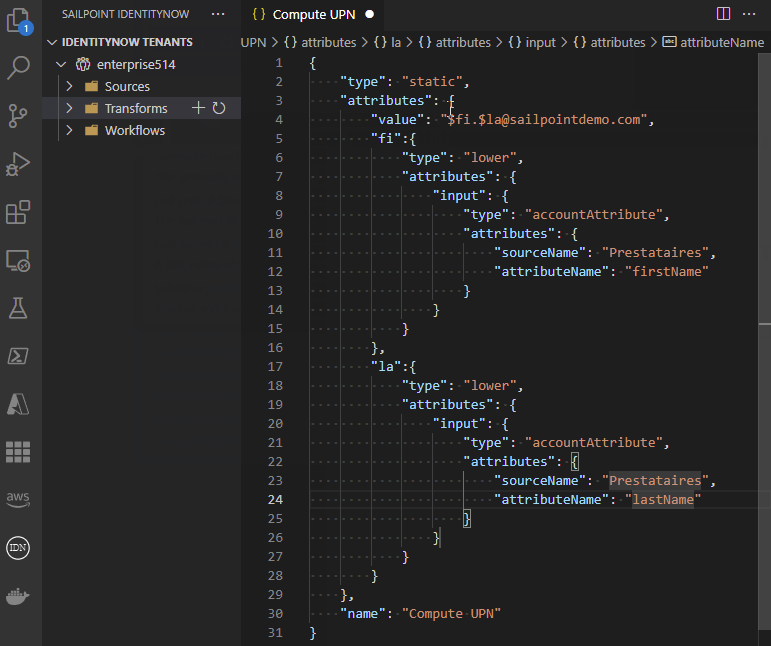
- View, create, edit, delete, and test transforms
- View, create, edit, delete provisioning policies of a source
- View, create, edit, delete schemas of a source
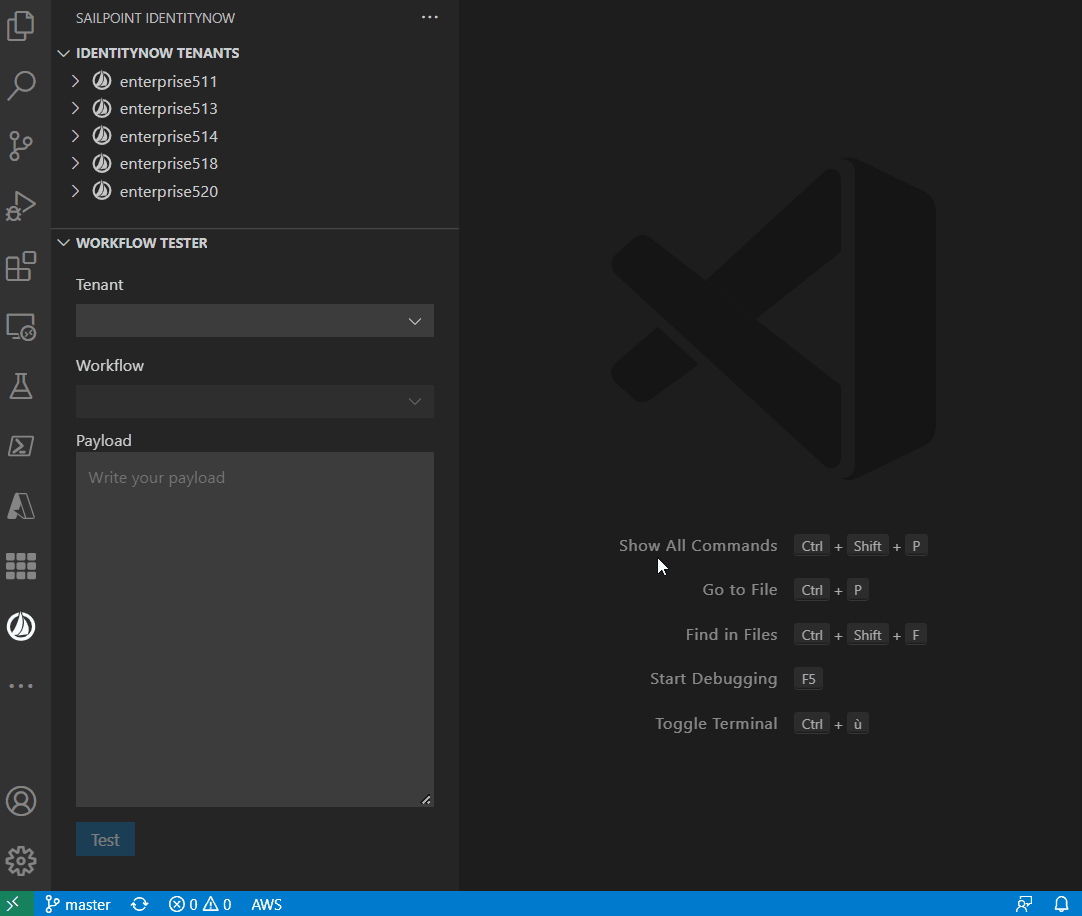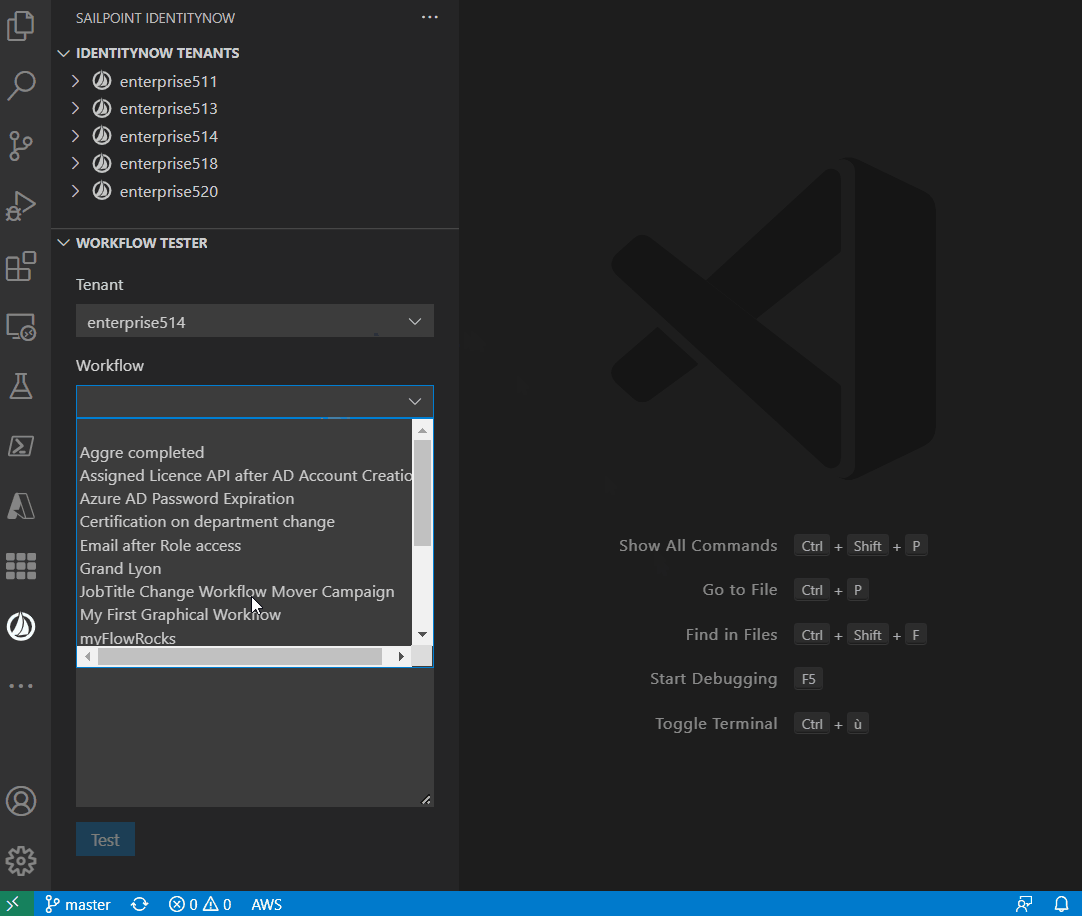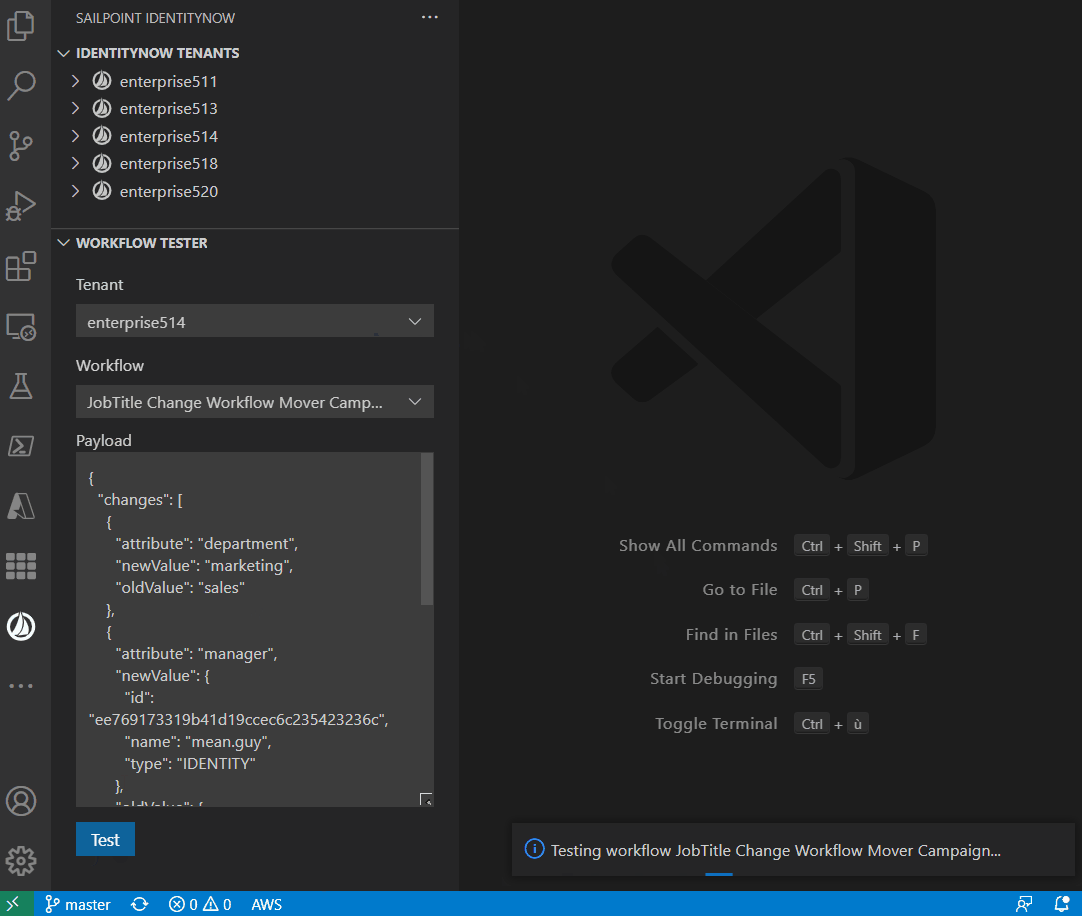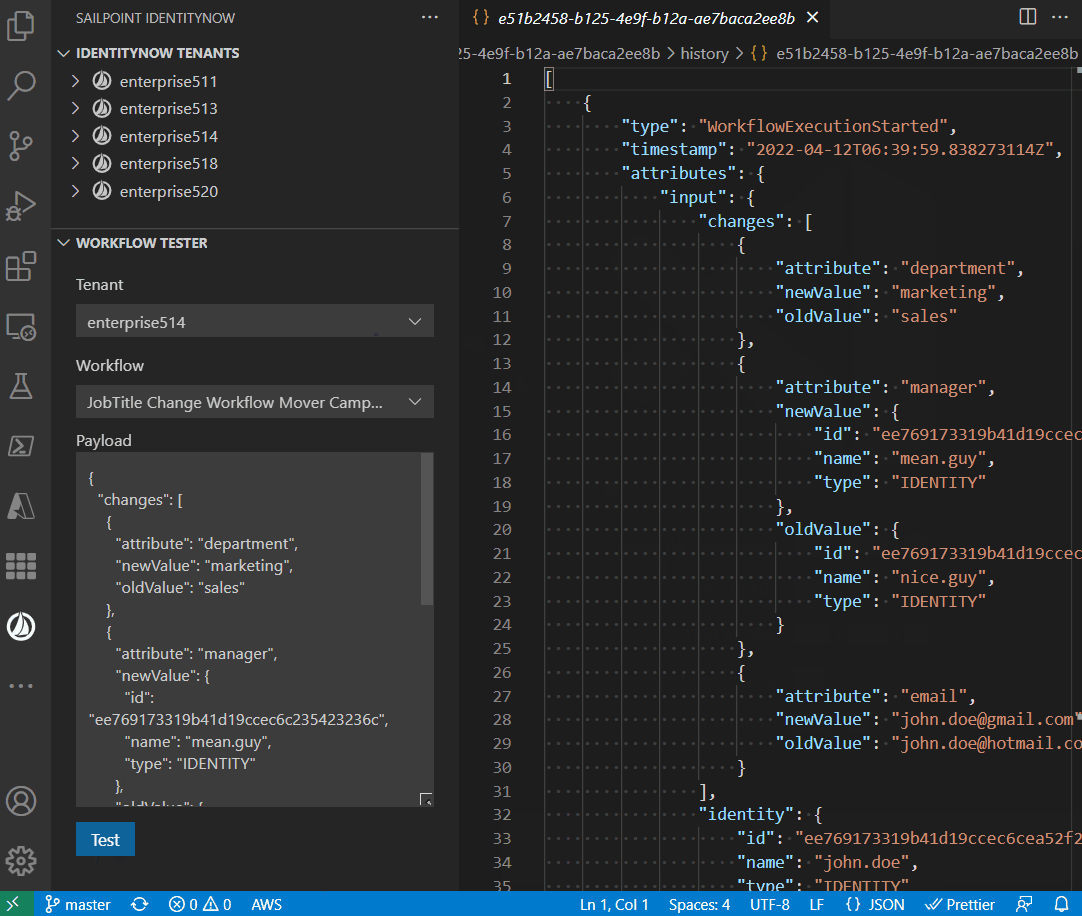
- View, edit, enable, disable, export, import and test workflows and view execution history
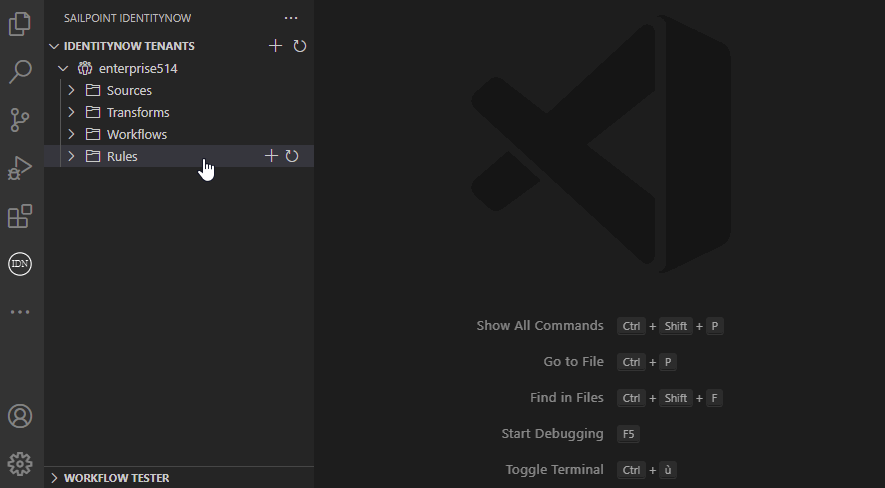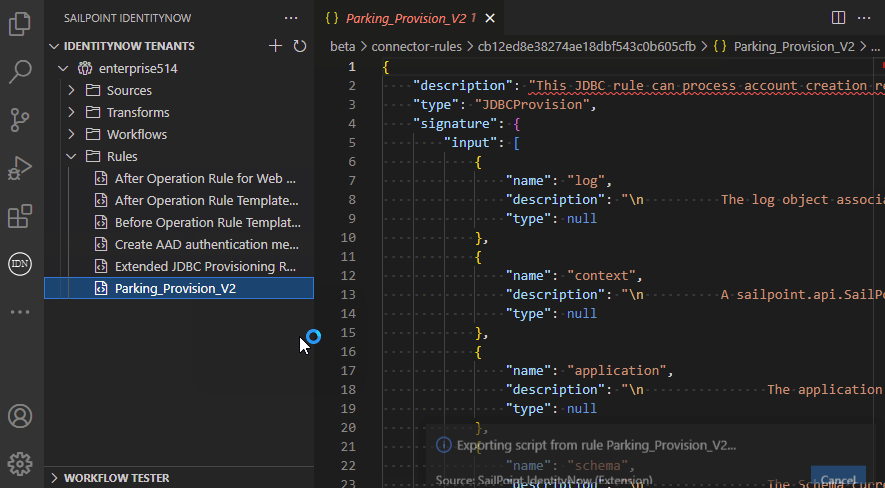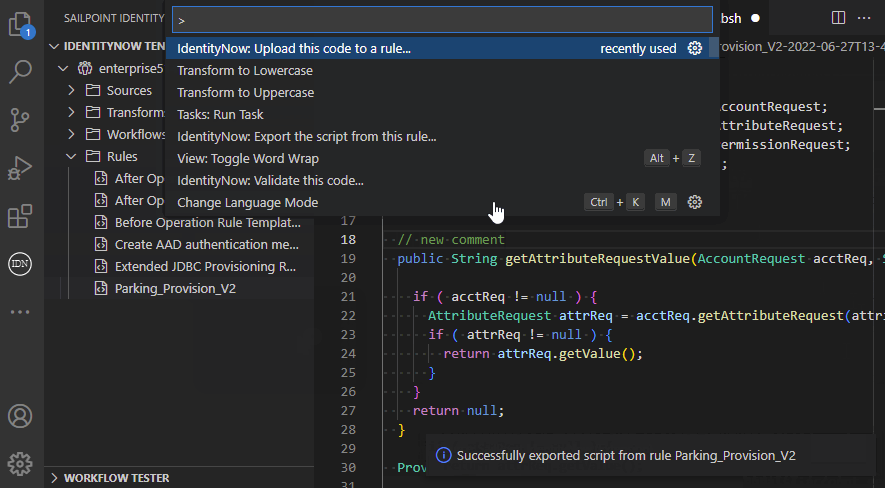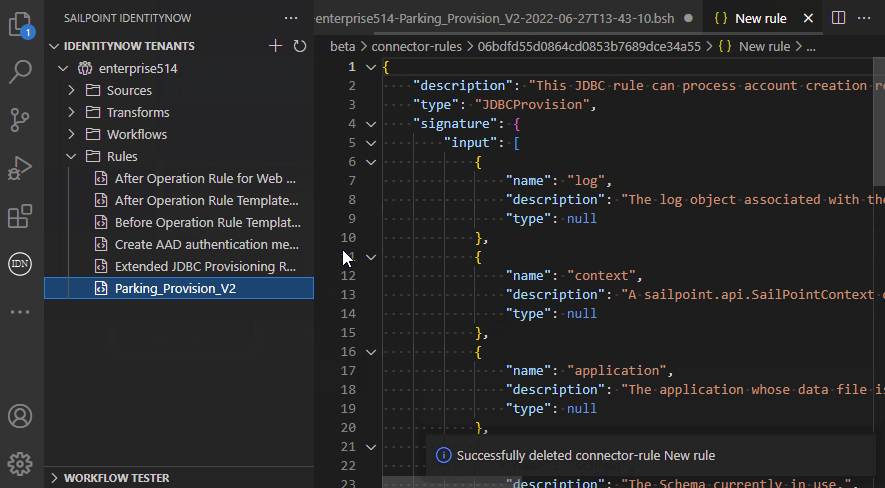
- View, create, edit, delete connector rules and export/import the script of a rule
- View, edit, delete service desk integrations
- View, edit, delete identity profiles and lifecycle states, and refreshes all the identities under a profile
- Import/Export Accounts (import for delimited files only), uncorrelated accounts, entitlement details
- View, edit, create, delete, export, import access profiles
- View, edit, create, delete, export, import roles
- View, edit, create, delete, export, import forms
- View, edit, create, delete search attribute config
- View, edit, create, delete identity attribute
- View, trigger attribute sync or process, delete identities
Go to the extension menu or press Ctrl+Shift+X and look for the extension "Identity Security Cloud". Click on the button Install.
The VSIX can be installed from the extension menu. Press Ctrl+Shift+X and in the menu, click Install from VSIX....
The extension supports several tenants.
Open the Command Palette with Ctrl+Shift+P (Windows or Linux) or Cmd+Shift+P (macOS) to find the command "ISC: Add tenant...".
Alternatively, you can click on the + in the SailPoint view.
You can add a tenant by using a Personal Access Token (PAT) or by using a short-lived access token (like one you can get from https://yourtenant.identitynow.com/ui/session).
It is also possible to add a tenant by using the following URIs:
vscode://yannick-beot-sp.vscode-sailpoint-identitynow/addtenant?tenantName=company&accessToken=eyJh...&authenticationMethod=AccessToken or
vscode://yannick-beot-sp.vscode-sailpoint-identitynow/addtenant?tenantName=company&clientId=806c451e057b442ba67b5d459716e97a&clientSecret=***&authenticationMethod=PersonalAccessToken.
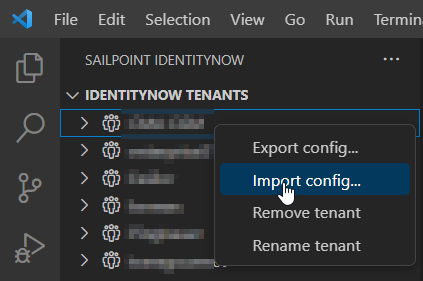
In the SailPoint view, right-click on a tenant to import or export config.
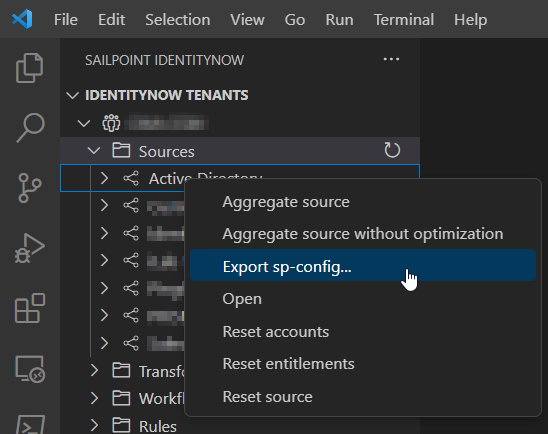
You can also export a single source, rule, identity profile or transform by right-clicking it and choosing "Export sp-config...".
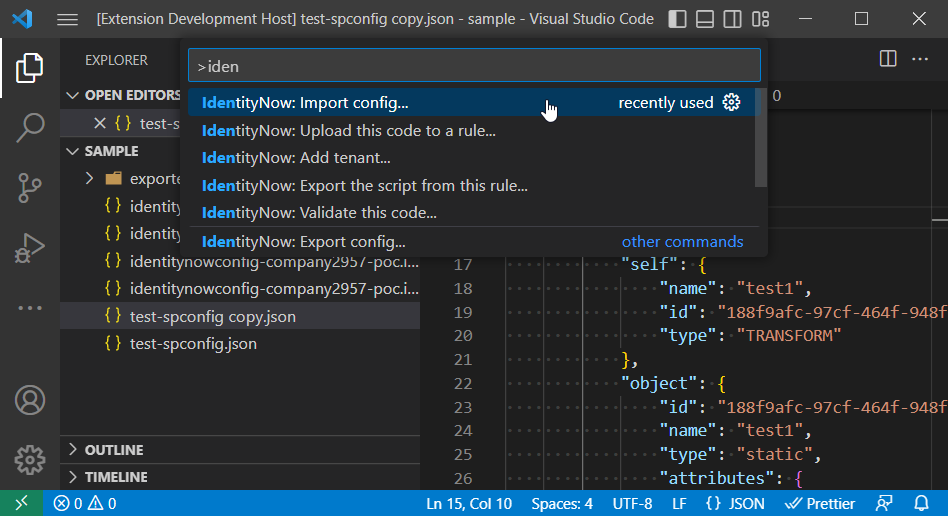
Or, from the Command Palette, find the command "ISC: Import config..." or "ISC: Export config...".
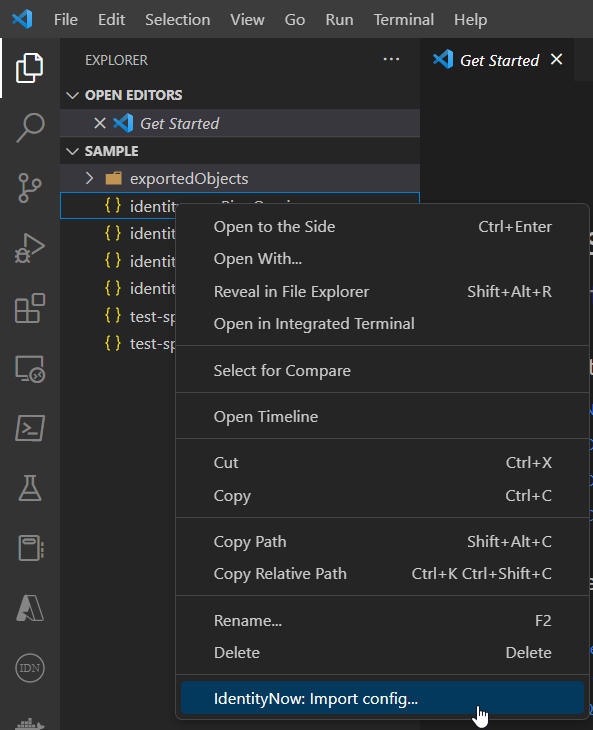
Finally, you can right-click a JSON file in the explorer to import it.
The extension allows you to manage rules and upload the script to a new or existing rule:
Export and Import workflows automatically:
- Remove the properties
created,creator,modified,modifiedBy, andowner - Nullify any value that starts with
$.secrets.
The extension allows you to test the workflow:
This extension includes the following snippets for transforms:
| Trigger | Content |
|---|---|
tr-acc |
Account Attribute |
tr-b64-dec |
Base64 Decode |
tr-b64-enc |
Base64 Encode |
tr-concat |
Concatenation |
tr-cond |
Conditional |
tr-date-comp |
Date Compare |
tr-date-format |
Date Format |
tr-date-math |
Date Math |
tr-diacritic |
Decompose Diacritial Marks |
tr-phone |
E164 Phone |
tr-first |
First Valid |
tr-rand-string |
Generate Random String |
tr-end |
Get End of String |
tr-refattr |
Get Reference Identity Attribute |
tr-id |
Identity Attribute |
tr-indexof |
Index Of |
tr-iso3166 |
ISO3166 |
tr-last-index |
Last Index Of |
tr-leftpad |
Left Pad |
tr-lookup |
Lookup |
tr-lower |
Lower |
tr-norm |
Name Normalizer |
tr-rand-alphanum |
Random Alphanumeric |
tr-rand-num |
Random Numeric |
tr-ref |
Reference |
tr-replace |
Replace |
tr-replace-all |
Replace All |
tr-rightpad |
Right Pad |
tr-rule |
Rule |
tr-split |
Split |
tr-static |
Static |
tr-sub |
Substring |
tr-trim |
Trim |
tr-upper |
Upper |
tr-uuid |
UUID Generator |
This extension includes the following snippets for schemas:
| Trigger | Content |
|---|---|
New schema |
Create a new schema |
New attribute |
Add new attribute |
This extension includes the following snippets for schemas:
| Trigger | Content |
|---|---|
New provisioning policy |
Create a new provisioning policy |
New field |
Create a new field |
This extension includes the following snippets for forms:
| Trigger | Content |
|---|---|
New Form Input |
Create a new form input |
This extension includes the following snippets for the Public Identities Configuration:
| Trigger | Content |
|---|---|
New identity attribute |
Create a new identity attribute mapping |
The following table provides the expected column for the CSV to import Access Profiles:
| Header | M1 | Description | Default Value |
|---|---|---|---|
name |
Yes | Name of the access profile | |
owner |
Yes | Owner of the access profile | |
source |
Yes | Source associated with the access profile | |
description |
No | Description of the access profile | null |
enabled |
No | Is the access profile enabled? | false |
requestable |
No | Is the access profile requestable? | false |
commentsRequired |
No | Require comments when the user requests access | false |
denialCommentsRequired |
No | Require comments when a reviewer denies the request | false |
approvalSchemes |
No | List of reviewers among APP_OWNER, OWNER, SOURCE_OWNER, MANAGER, or the name of the governance group separated by ; |
[] (No approval) |
revokeApprovalSchemes |
No | List of reviewers among APP_OWNER, OWNER, SOURCE_OWNER, MANAGER, or the name of the governance group separated by ; |
[] (No approval) |
entitlements |
No | Entitlements of the access profile | [] |
The following table provides the expected column for the CSV to import Roles:
| Header | M1 | Description | Default Value |
|---|---|---|---|
name |
Yes | Name of the role | |
owner |
Yes | Owner of the role | |
description |
No | Description of the role | null |
enabled |
No | Is the role enabled? | false |
requestable |
No | Is the role requestable? | false |
commentsRequired |
No | Require comments when the user requests access | false |
denialCommentsRequired |
No | Require comments when a reviewer denies the request | false |
approvalSchemes |
No | List of reviewers among OWNER, MANAGER, or the name of the governance group separated by ; |
[] (No approval) |
revokeCommentsRequired |
No | Require comments when the user requests revocation | false |
revokeDenialCommentsRequired |
No | Require comments when a reviewer denies the revocation request | false |
revokeApprovalSchemes |
No | List of reviewers among OWNER, MANAGER, or the name of the governance group separated by ; |
[] (No approval) |
accessProfiles |
No | List of access profiles | [] |
membershipCriteria |
No | Membership criteria for automatic assignment |
membershipCriteria follows kind of SCIM filters
There are 3 kind of attributes:
- Identity Attribute: the format is
identity.{attribute name}. Ex:identity.cloudLifecycleState,identity.type, etc. - Account Attribute: the format is
{source name}.attribute.{attribute name}. If the source name contains space, the source name must be put between quotes or double-quotes - Entitlements: the format is
{source name}.entitlement.{attribute name}. If the source name contains space, the source name must be put between quotes or double-quotes
| Operator | Description |
|---|---|
| eq | equals |
| ne | not equals |
| co | contains |
| sw | starts with |
| ew | ends with |
| Operator | Description |
|---|---|
| and | Logical "and" |
| or | Logical "or" |
Values must be within " or '.
Expressions can be grouped by using parenthesis. Parenthesis are mandatory for 3-level expression but are optional otherwise.
Here are a few examples extracted from the unit tests:
identity.department eq 'Customer Service' and identity.cloudLifecycleState eq 'active'
'Active Directory'.entitlement.memberOf eq 'CN=Accounting,OU=Groups,OU=Demo,DC=seri,DC=sailpointdemo,DC=com' and 'Active Directory'.attribute.departmentNumber eq '1234'
(identity.department eq 'Customer Service' and identity.cloudLifecycleState eq 'active') or (identity.cloudLifecycleState eq 'active' and identity.jobTitle co 'Accounts Payable Analyst')
The extension supports the following settings:
vscode-sailpoint-identitynow.report.accessProfiles.filename: Define the pattern for the folder to export access profiles.- Default value:
%x/reports/%T-AccessProfiles-%y%M%d-%h%m%s.csv
- Default value:
vscode-sailpoint-identitynow.report.accounts.filename: Define the pattern for the folder to export accounts.- Default value:
%x/reports/%T-%S-Accounts-%y%M%d-%h%m%s.csv
- Default value:
vscode-sailpoint-identitynow.report.uncorrelatedAccounts.filename: Define the pattern for the folder to export uncorrelated accounts.- Default value:
%x/reports/%T-%S-Uncorrelated-Accounts-%y%M%d-%h%m%s.csv
- Default value:
vscode-sailpoint-identitynow.report.entitlements.filename: Define the pattern for the folder to export entitlement details.- Default value:
%x/reports/%T-%S-Entitlements-%y%M%d-%h%m%s.csv
- Default value:
vscode-sailpoint-identitynow.report.roles.filename: Define the pattern for the folder to export roles.- Default value:
%x/reports/%T-Roles-%y%M%d-%h%m%s.csv
- Default value:
vscode-sailpoint-identitynow.sP-Config.singleResource.filename: Define the pattern for the SP-Config file of a single resource (Source, Identity Profile, Connector Rule, or Transform).- Default value:
%x/exportedObjects/identitynowconfig-%t-%S-%y%M%d-%h%m%s.json
- Default value:
vscode-sailpoint-identitynow.sP-Config.singleFile.filename: Define the pattern for the SP-Config file as a single file for multiple resources- Default value:
%x/exportedObjects/identitynowconfig-%t-%y%M%d-%h%m%s.json
- Default value:
vscode-sailpoint-identitynow.sP-Config.multipleFiles.folder: Define the pattern for the SP-Config folder as multiple files for multiple resources. This folder is proposed.- Default value:
%x/exportedObjects
- Default value:
vscode-sailpoint-identitynow.sP-Config.multipleFiles.filename: Define the pattern for the SP-Config filename as multiple files for multiple resources. It will be concatenated to the export folder. These filenames are not confirmed.- Default value:
%o/%S.json
- Default value:
vscode-sailpoint-identitynow.export.forms.filename: Define the pattern to export all forms of a tenant- Default value:
%x/Forms/Forms-%t-%y%M%d-%h%m%s.json
- Default value:
vscode-sailpoint-identitynow.export.form.filename: Define the pattern to export a single form from a tenant- Default value:
%x/Forms/Form-%t-%S-%y%M%d-%h%m%s.json
- Default value:
vscode-sailpoint-identitynow.export.workflow.filename: Define the pattern to export a single workflow from a tenant- Default value:
%x/Workflows/Workflow-%t-%S-%y%M%d-%h%m%s.json
- Default value:
vscode-sailpoint-identitynow.treeView.pagination: Define the number of roles and access profiles that are displayed in the tree view- Default value: 100
The patterns defined above use the following tokens:
%u: User Home Dir%w: Workspace folder%x: Either workspace folder if defined, or home dir%d: Day%M: Month%y: Year%h: Hour%m: Minute%s: Second%t: Tenant name%T: Tenant display name%o: Object type%S: Source name for source-based report or object name
- Updated schema for lifefycle state (
identityState) - Filtering server-side for uncorrelated accounts
- Added transforms "RFC5646" and "Display Name" (cf. #87)
- Add validation of read-only during SP-Config import
- Can create or delete an identity attribute (cf. #83)
- Fixed issue during the account reset (cf. #85)
- 429 Too Many Requests error during export or import of roles and access profiles (cf. #82)
- Role and Access Profile imports are now cancellable
- Update for source aggregation and reset to leverage beta endpoints instead of CC endpoints
- Add searching and viewing identities by @henrique-quintino-sp (cf. #74)
- Add attribute sync, process and delete command on identities by @henrique-quintino-sp (cf. #74)
- Fixed normalizeNames (cf. #73)
- Lock tenant as read-only to prevent any change (cf. #75 and #81)
- Fixed with generate digit token to use the username and not the account name
- Automatically update workflow if its status is changed
- Fixed case where a single entitlement or single access profiles is returned during role creation
- Add new command to edit connector rule (Edit script)
- Changing IdentityNow to Identity Security Cloud/ISC
- Logging every call to ISC
- Catch error message if peek objects fails
- Edit Password Org Config
- Generate a digit token for password reset
- 404 error when sources had '/' in their name (cf. #71)
- New attempt to publish extension
- Refactoring of IdentityNowTreeItem.ts and fixed refreshing issue with Workflows
- Non-matching schema for lifecycle states
- Publication issue
- Could not open Identity Attributes from several tenants (cf. #69)
- Transform not correctly saved (cf. #68)
- Import/Export entitlements for roles
- Add support for Search attribute config (cf. #64)
- Add support for Identity Attributes
- Display warning if file is too big (cf. #66)
- Export/Import workflows (cf. #57)
- Edit Public Identities Config
- Edit Access Request Configuration
- Can export everything with SP-Config (cf. #56)
- Can select cloud rules for export with SP-Config
- Add IDENTITY_OBJECT_CONFIG as an importable object from SP-Config
- Add support for Forms
- Clone a source (cf. #60)
- Export of roles and access profiles without owner
- Fix pagination during export of roles and access
- Add the command "Ping Cluster" on sources by @henrique-quintino-sp (cf. #61)
- Export of roles was failing due to 1-level Membership Criteria
- Pagination during export
- In some unknown condition, source may not have a name. In such case, the source is filtered
- View, edit, create, delete, export, import access profiles with the help of @richastral (cf. #55)
- View, edit, create, delete, export, import roles with the help of @richastral (cf. #55)
- Upgrade sailpoint-api-client dependency
- Honor delimiter parameter for account export
- Add better error message when resetting a source fails (cf. #54)
- Issue when importing SP-Config: when selecting items, the list of object Ids was not properly sent
- Issue when refreshing identities of an identity profile (cf. #53)
- Provide the ability to create provisioning policy for something else than the CREATE policy (cf. #29)
- Issue when creating a provisioning policy (cf. #52)
- Revert bundle (cf. #51)
- Issue with fetch (cf. #50)
- Remove dependency to client-oauth2, isomorphic-fetch, isomorphic-form-data
- Relies on axios and sailpoint-api-client wherever it is possible
- Better error management for SPConfig import and object type displayed for import
- Workflow icon not properly updated after enabling or disabling the workflow
- New command: Aggregation of entitlements
- Settings for export path, including SP Config
- New command: Export of accounts
- New command: Export of uncorrelated accounts
- New command: Export of entitlement details
- New command: Import of accounts
- New command: Import of uncorrelated accounts
- New command: Import of entitlement details
- Better error management of SPConfig Import and message info
- List transforms by name while exporting SP-Config
- Export was not creating folders recursively
- Update schema for identity profiles, life cycle states, and provisioning policies
- Update regexp for tenant name for short names
- Update length limit for connector rule names and provisioning policy name
- Update regexp for tenant name
- Fix TLS error when trying to get an access token
Almost Christmas!
- Capability to export a single source, rule, transform or identity profile from the tree view
- Capability to refine export from the command palette or from a tenant in the tree view
- Capability to import a sp-config
- Can refresh identities under an identity profile (cf. #30)
- Fix error when exporting to file (cf. #35)
- Add supports for Service Desk Integrations (@fernando-delosrios-sp)
- Fix supports of UTF-8 values in transform (cf. #33)
- Add 2 commands for sources: reset accounts and reset entitlements
- Add support for Identity Profiles
- Pagination for sources (cf. #25)
- Regression on transform evaluation (cf. #20)
- Possibility to add a tenant with an access token (cf. #18)
- The extension have an URI handler (cf. #17). If a URL with the following format is called in the system, a tenant is added or updated: vscode://yannick-beot-sp.vscode-sailpoint-identitynow/addtenant?tenantName=XXX&accessToken=eyJh...&authenticationMethod=AccessToken
- Can rename tenant display name (cf. #12)
- Support for connector rules: creation, deletion, update, export, import
- Aggregation without optimization was not working properly
Transforms for ever!
- New transforms (E.164 Phone, Random Alphanumeric Random Numeric, Replace All, Rule, UUID Generator), cf. #8
- #6 update regexp for transform names
Transforms are the best!
Added:
- Add step to creation of transform to have a non-empty file
- If only 1 tenant, automatically selected in the workflow tester
- Added refresh buttons in the view
- Add the capacity to evaluate transforms #7 thanks to @cristian-grau-sp
Fixed:
- Regexp for provisioning policy
- Issue #3 with new transform
Fixed:
- Regexp for tenant, with or without domain
- Remove PAT when removing tenant
- Fix regexp for PAT secret
Workflows for ever!
- Export of tenant config
- Add support for workflows
- Add workflow tester
Let's make transform great again!
- Add support for source schemas
- Add support for provision policies
- Add schema and snippets for source schemas
- Add schema and snippets for provisioning policies
- Add snippets for transforms
Initial internal release
- Add tenant with Personal Access Token (PAT) authentication
- Remove tenant
- Open Sources and Transforms
- Save Sources and Transforms
- Create Transform
- Remove Transform